ISMS: a well defined approach towards organizational security
The answer lies in the realization that the most important factor of Information Security is not the technical components, but the people who manage those components, be it your security devices, databases or desktops.
A well-defined Information Security Initiative has the following components:
- Senior Management Support.
- An Organizational Security Policy endorsed by the Senior Management.
- Technical Guidelines for the IT Department.
- Guidelines for Employees on Safe and Secure practises at the workplace - choosing good passwords, configuring screen saver time-outs etc.
- Sound Network Design, which includes firewalls, Intrusion Detection Systems, Comprehensive Anti- Virus Protection etc.
- Periodic and Specific Training modules for Management, Employees and IT department.
- Business Continuity Plan and Disaster Recovery Plan to keep essential business functions running in case of a disaster.
- Continuous and Periodic Evaluation of the Policies, Technical components and Employee Practises
Information Security Management Systems
Information Security Management Systems (ISMS) is a well-proven framework to initiate, implement, maintain and manage information security within any organization. A good ISMS program is a healthy combination of "Process Oriented" and "Technical" CONTROLS (safeguards), implemented to provide a high-level of Security for Business Critical Data.
How do you go about building ISMS in your Organization?
Implementation of Information Security Management Systems can be broken down into well-defined step-wise modules.
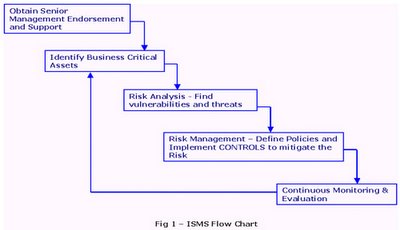
Step 1 – Gather Senior Management Support
The most important factor, which ensures the success of an ISMS initiative, is support of the wise men sitting around the boardroom table. The advantages of this are manifold:
- Senior Management will look at Information Security as a business case and not as a technical subject.
- Senior Management realizes responsibility towards business partners and shareholders more, as Information Security is about protecting the confidentiality of Business Critical Data and hence the reputation of the organization.
- Employees co-operate more in Information Security Initiatives knowing that the Senior Management drives the initiative.
Step 2 – Identify Business Critical Assets
The Senior Management along-with other departments identifies the assets which are most critical to keep the business running in a viable and profitable condition. Examples of business critical assets are "Reputation of the Organization, Database and ERP Servers, Internet Link, Employees".
Once the critical assets are identified, resources are earmarked for protecting these Business Critical Assets.
Step 3 - Conduct a Risk Analysis
"Once we know our weaknesses, they cease to do us any harm." G.C.Lichtenberg (1742–1799), German Physicist and Philosopher
Use a third party security consultant to gather a non-prejudiced understanding of risks of your assets being compromised. This is accomplished through vulnerability assessments, physical audits etc. In Information Security Parlance Vulnerability is a weakness, Threat is something, which can exploit the vulnerability, and Risk is the possibility of the threat exploiting the vulnerability. A Sample is shown below:
Asset – Database Server
Vulnerability – Lack of Anti-Virus
Threat – Virus or Worm
Risk – Probability of Virus or Worm attacking the Server
Exposure – Virus Attack
Step 4 – Risk Management
"If you know the enemy and know yourself, you need not fear the result of a hundred battles."
Chinese Warlord Sun Tzu, Author of "The Art of War"
Risk Management involves:
- Designing and Implementing Safe-Guards (CONTROLS) to protect Business Critical Assets.
- Controls are "Process Oriented" (Policies, Training) and "Technical Components" (Security Devices)
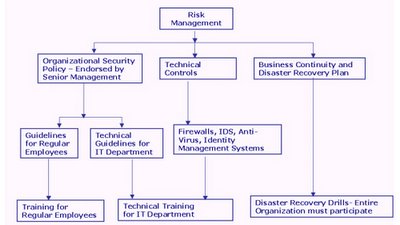
Fig 2 – Risk Management Flow Chart
Given below is a sample implementation of Technical Controls (Sound Network Design and Security Devices):
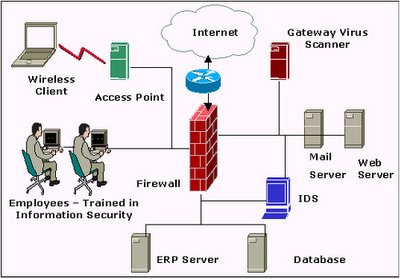
Fig 3 – Sample Implementation of Technical Controls (Security Devices)
Business Continuity Planning and Disaster Recovery Planning
An important component of Risk Management is Business Continuity and Disaster Recovery Plan, which are essential to ensure that your business continues even in the face of an unfavourable event such as a Natural Disaster, Attacks or any unforseen incident.
Business Continuity Plan is developed by an organization to outline plans to keep the business critical assets functioning in case of a disaster.
Disaster Recovery Plan (DRP) is the sequence of actions implemented after the disaster and is a part of the Business Continuity Plan. DRP essentially deals with protecting human lives in case of a disaster, salvage operations and restoration of business functions.
Step 5 – Continuous Monitoring and Evaluation
A well-designed and executed ISMS is only as good as it's up-keep. Periodic Audits and Assessments are essential to ensure that the ISMS is healthy and not stagnant.
Importance and Relevance of ISMS to your business
A well-defined ISMS ensures that you are complying with internationally recognized Standards in Information Security and Privacy. Some of the standards and regulations, which focus on well-defined ISMS are:
BS7799/ISO 17799 – Is an Internationally Recognized standard in Information Security Management Systems.
Health Insurance Portability Accountability Act (HIPAA) – U.S National Standards to Protect the Privacy of Personal Health Information.
GLBA (Gramm-Leach-Bliley Act) – U.S. Government Act that governs the collection and disclosure of customers' personal financial information by financial institutions.
Text by Anup Narayanan, member of the ISMS PT Community and independent Information Security Consultant, could be reached at:
anup@athenainfosec.com.
Labels: Segurança da Informação
Data 9.11.05
![]()

