ISO 27001 methodology
ISO 27001 (former BS 7799-2) presents the requirements to implement and operate an Information Security Management System (ISMS). Bellow, there is interpretation of the major requirements and deliverables of each phase of the ISMS implementation method established by ISO 27001.
1 - Define the ISMS scope
1.1 Major requirements
a) Delimitation of the ISMS scope using a documented procedure;
b) Identification of legal and business requirements and constraints;
c) Identification of the information assets within the ISMS scope.
1.2 Required outputs
a) Scope statement (description of what the scope is);
b) List of legal and business requisites and constraints;
c) List of information assets,
a) Delimitation of the ISMS scope using a documented procedure;
b) Identification of legal and business requirements and constraints;
c) Identification of the information assets within the ISMS scope.
1.2 Required outputs
a) Scope statement (description of what the scope is);
b) List of legal and business requisites and constraints;
c) List of information assets,
2 - Define the ISMS policy
2.1 Major requirements
The document entitle of Information Security Policy should include:
a) definition of objectives of information security;
b) management statement in support;
c) reference to other internal security regulations (e.g. procedures);
d) identification of legal requirements;
e) responsibilities for management;
f) references to other documents.
a) definition of objectives of information security;
b) management statement in support;
c) reference to other internal security regulations (e.g. procedures);
d) identification of legal requirements;
e) responsibilities for management;
f) references to other documents.
2.2 Required outputs
a) Information security policy document;
b) Specific policies (if applicable);
c) Standards, procedures, guidelines (if applicable).
3 - Define a risk assessment approach
a) Information security policy document;
b) Specific policies (if applicable);
c) Standards, procedures, guidelines (if applicable).
3 - Define a risk assessment approach
3.1 Major requirements
A risk assessment method must be:
a) systematic and;
b) suitable to the ISMS and legal requirements.
b) suitable to the ISMS and legal requirements.
3.2 Required outputs
Definition of the formula type of risk calculation.
4 - Identify the risk
4.1 Major requirements
a) Identify the threats to assets;
b) Identify the vulnerabilities that might be exploited by those threats;
c) Identify the impacts that losses of CIA dimensions on assets.
b) Identify the vulnerabilities that might be exploited by those threats;
c) Identify the impacts that losses of CIA dimensions on assets.
4.2 Required outputs
A list of risks.
A list of risks.
5 - Analyze and evaluate the risk
5.1 Major requirements
To calculate the risk, it should be consider:
a) Business impact of a security failure, taking into account the losses on CIA dimensions;
b) Likelihood of it.
b) Likelihood of it.
5.2 Required outputs
A calculated risk level (an estimation of the probability and impact of a risk).
6 - Identify and evaluate options for the treatment of risks
6.1 Major requirements
The risk may be:
a) accept it;
b) avoid it;
c) transfer it to insurers or suppliers;
d) reduce it.
b) avoid it;
c) transfer it to insurers or suppliers;
d) reduce it.
6.2 Required outputs
Risk treatment decision (in terms of the 4 strategies defined above).
Risk treatment decision (in terms of the 4 strategies defined above).
7 - Select control objectives and controls for the treatment of risk
7.1 Major requirements
The risk treatment plan should include:
a) Mandatory measures from BSI´s chapters 4, 5, 6 and 7.
b) Selective measures from Annex A that may be chosen or excluded.
c) Measures derived from other sources, as long as they provide more assurance than the BSI`s controls.
a) Mandatory measures from BSI´s chapters 4, 5, 6 and 7.
b) Selective measures from Annex A that may be chosen or excluded.
c) Measures derived from other sources, as long as they provide more assurance than the BSI`s controls.
7.2 Required outputs
Risk treatment plan (defines for each risk, its strategy, and if this decision is to reduce, includes appropriate controls).
Risk treatment plan (defines for each risk, its strategy, and if this decision is to reduce, includes appropriate controls).
8 - Prepare a Statement of Applicability
8.1 Major requirements
Produce a Statement of Applicability (with the reasons for the choice of controls or its exclusion).
8.2 Required outputs
Statement of Applicability (SoA).
9 - Obtain management approval
Statement of Applicability (SoA).
9 - Obtain management approval
9.1 Major requirements
a) Approve residual risks;
b) Authorization to operate the ISMS.
b) Authorization to operate the ISMS.
9.2 Required outputs
a) Residual risks approved;
b) ISMS operation authorization.
b) ISMS operation authorization.
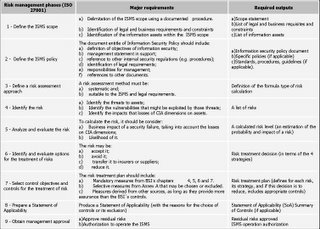
Summary of ISO 27001 methodology
Text by Paulo Coelho
Information Security Consultant at Sinfic, SA.
Labels: Segurança da Informação
Data 12.1.06
![]()

